- CrowdStrike reveals the causes of the bug that crashed 8.5 million Windows PCs
- More than 10,000 million passwords exposed in leaks have just been published on a forum
A “mystery malware” destroys half a million routers in less than 72 hours, wreaking havoc on the infrastructure of a major Internet service company (ISP). The situation affected Windstream, a US company, in October last year. The details have come to light in the last few hours thanks to the publication of a report made by the security firm Lumen Technologies Black Lotus Lab. This document details everything that happened on October 25, 2023, in which more than half a million routers were completely inoperative in an event that can be considered catastrophic.
This cyberattack left hundreds of thousands of users without an internet connection, and has generated significant alarm among cybersecurity experts. The sophistication and speed of the attack have been a cause for concern, as it evidences an unprecedented level of coordination and precision. Preliminary investigations suggest that the malware was specifically designed to exploit vulnerabilities in devices on the affected ISP’s network.
Devastating impact on infrastructure after the destruction of 600,000 in a matter of hours
In a span of 72 hours, the malware managed to disable approximately 600,000 routers, representing a sizable fraction of the operational devices on the ISP’s network. This level of destruction is unusual and has led to a swift response from authorities and security experts. The affected PSI is working closely with incident response teams and cybersecurity companies to mitigate the damage.
Investigations are ongoing to identify the exact origin and purpose of the malware. Although it has not yet been determined who is behind this attack, the coordinated nature of it suggests the possibility of an operation backed by a state or an organized criminal group. Experts are analyzing samples of the malware to better understand how it works and develop effective countermeasures.
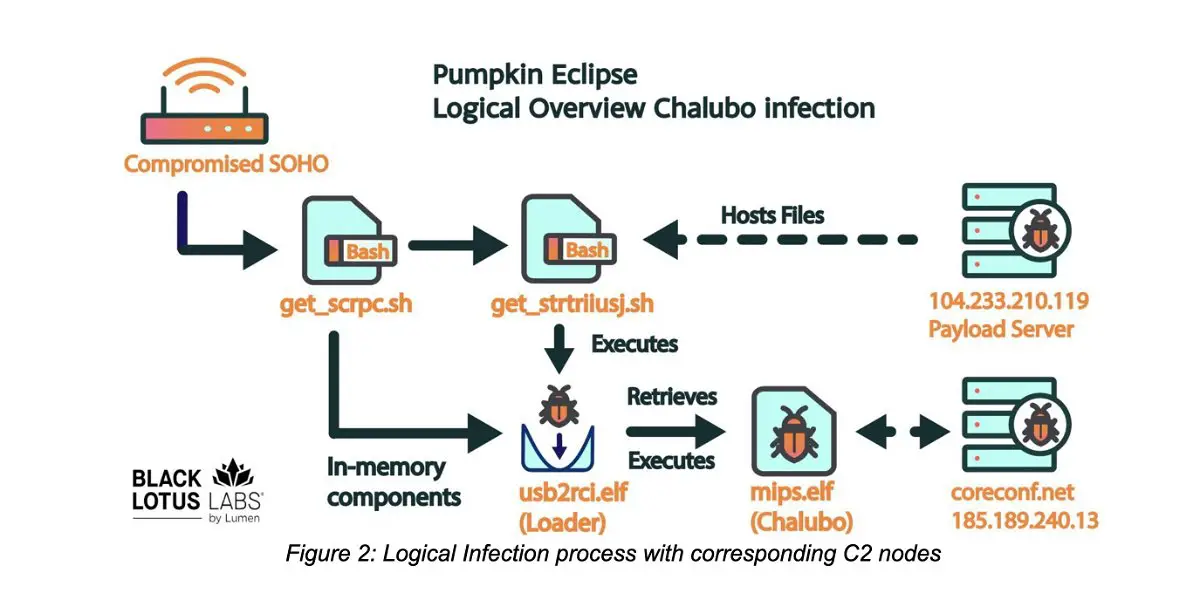
Among the affected routers are 179,000 and 480,000 models of ActionTec and Sagemcom respectively. The extent of the damage already inflicted means that the recovery process has been complex and protracted. In addition, to erase the traces of the attack, a malware known as “Chalubo” has been used to trigger scripts that overwrite the router’s firmware.
The worst thing about this whole situation is that it is completely unknown how this massive infection could have been carried out. The researchers indicate that there is still a lot of work ahead to determine how it has been operated because the vulnerabilities of these affected routers are unknown.

Comments